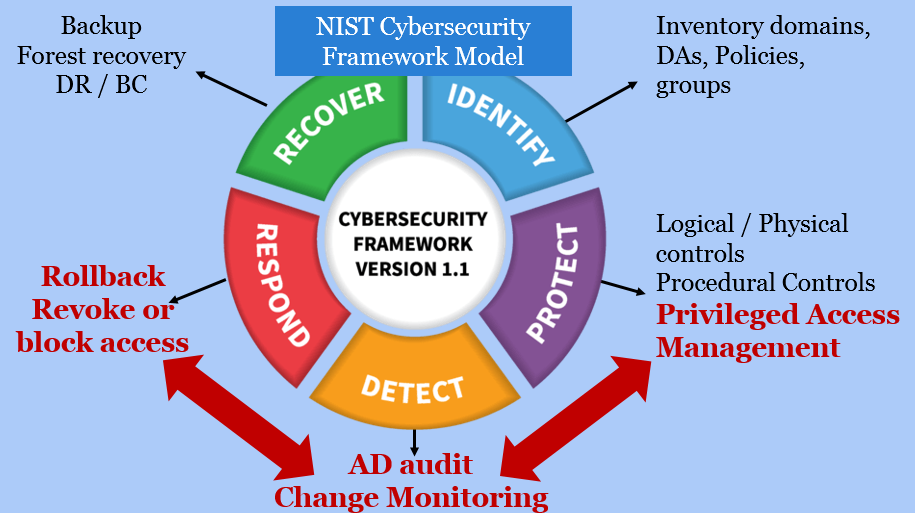
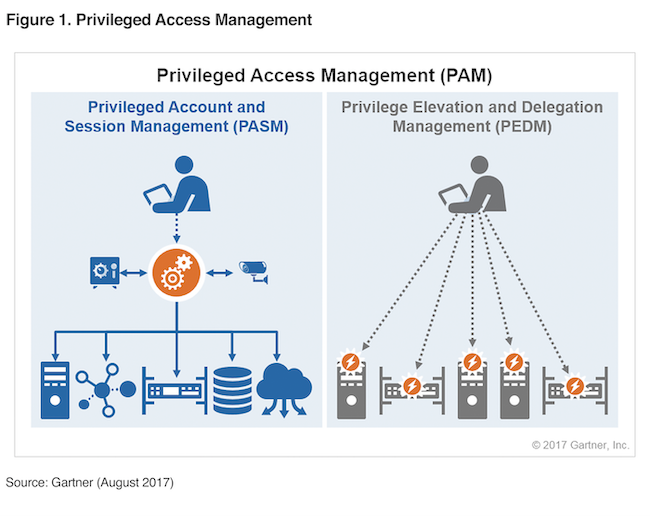
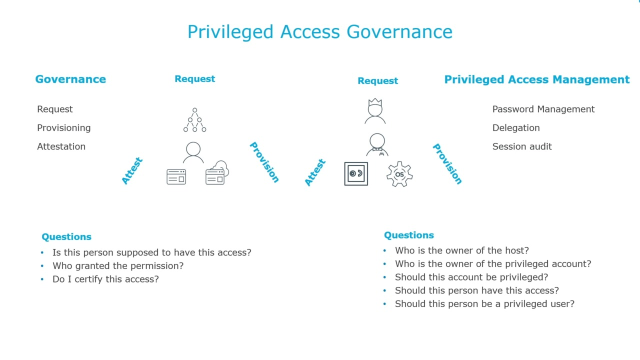
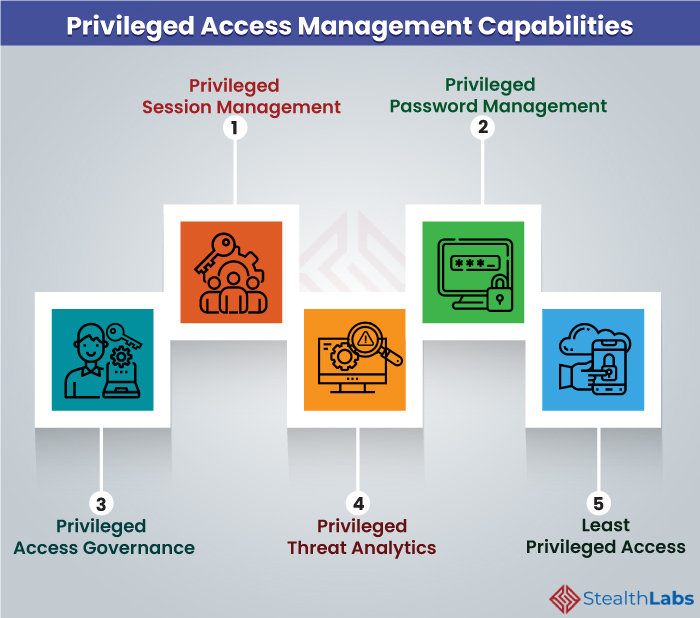
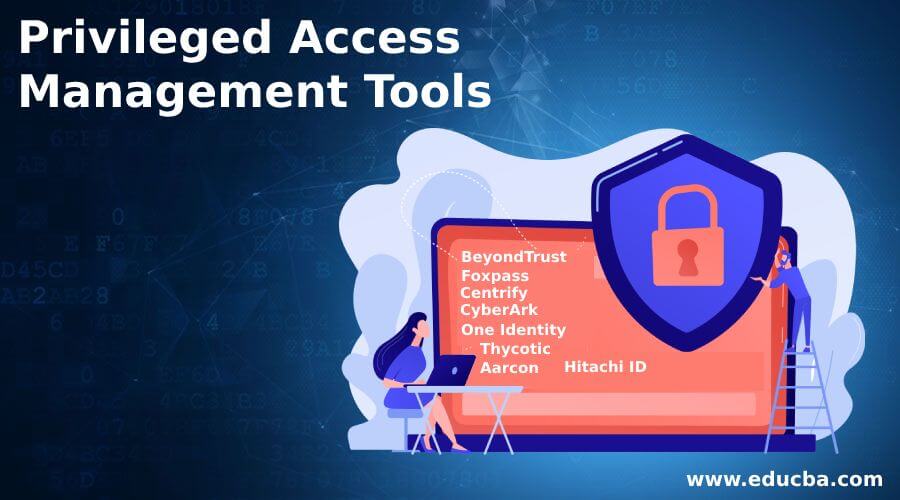
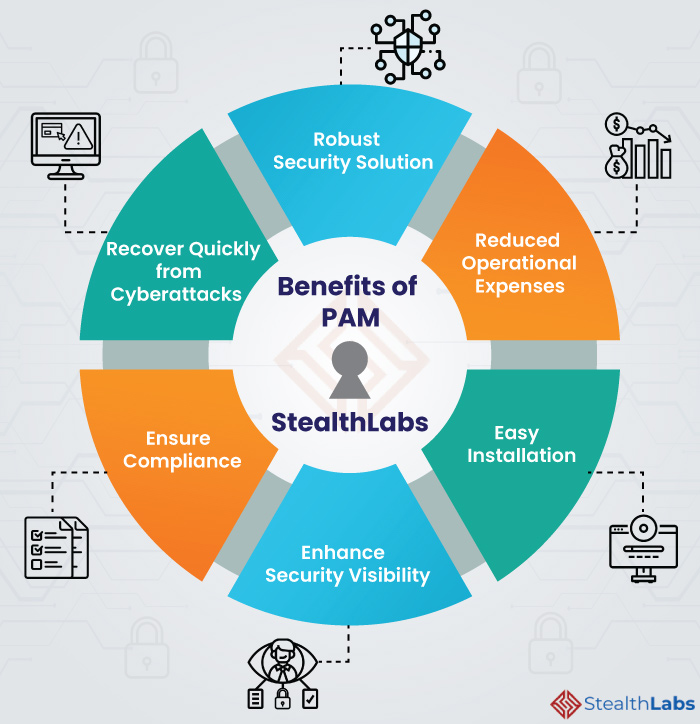
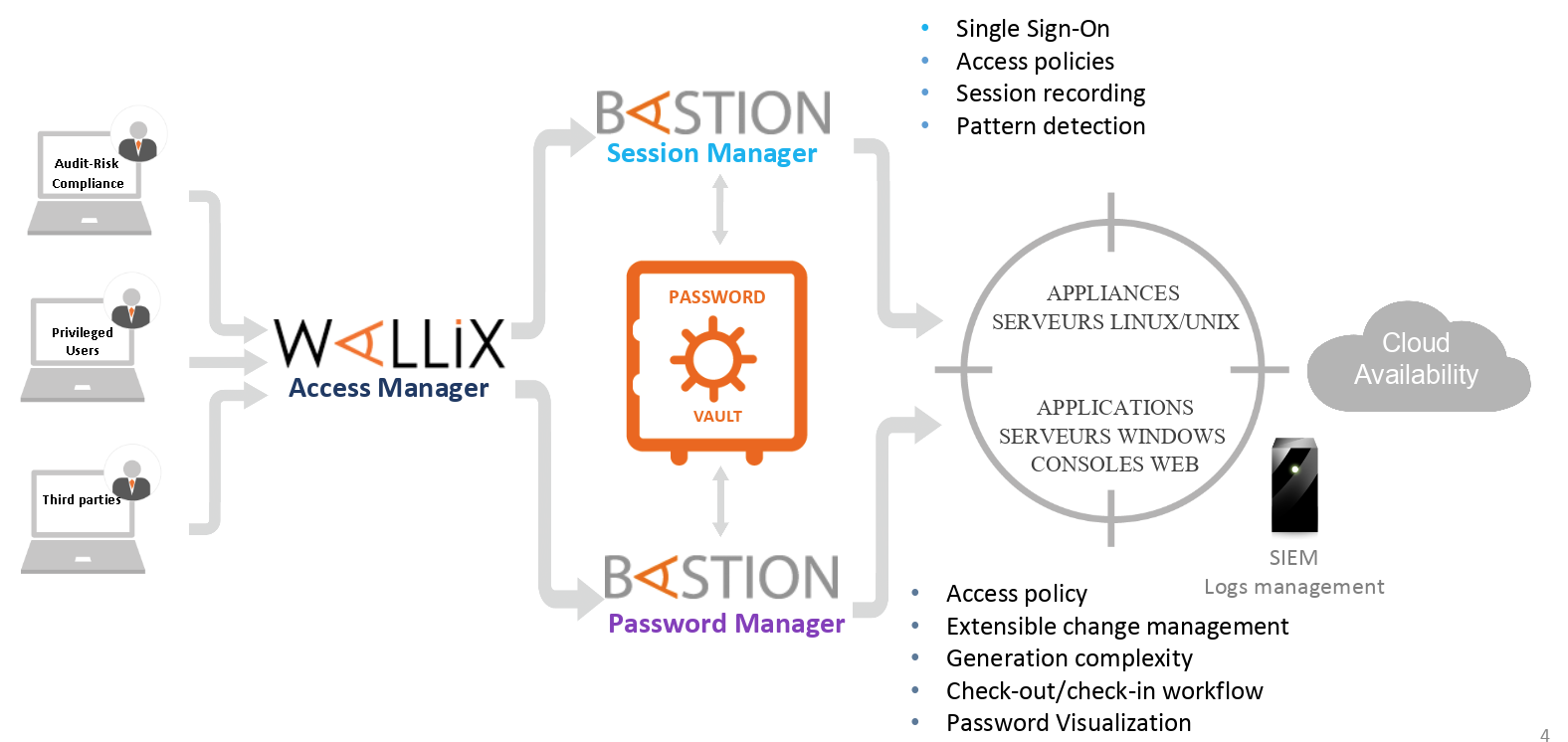
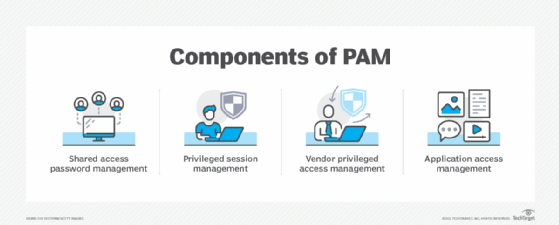
What is Privileged Access Management (PAM)? Read the Definition in our Security Glossary | BeyondTrust
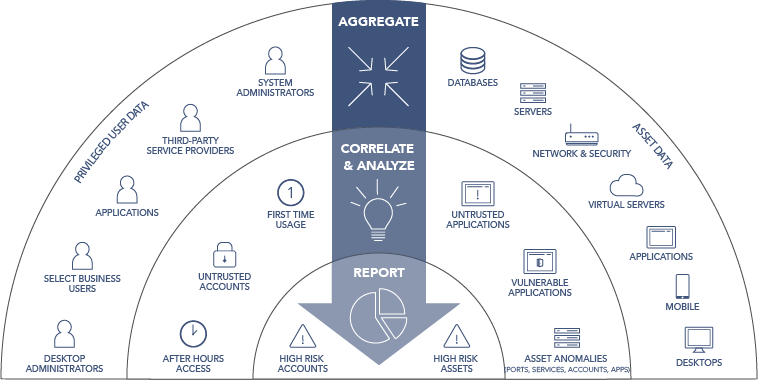
What is Privileged Access Management (PAM)? Read the Definition in our Security Glossary | BeyondTrust
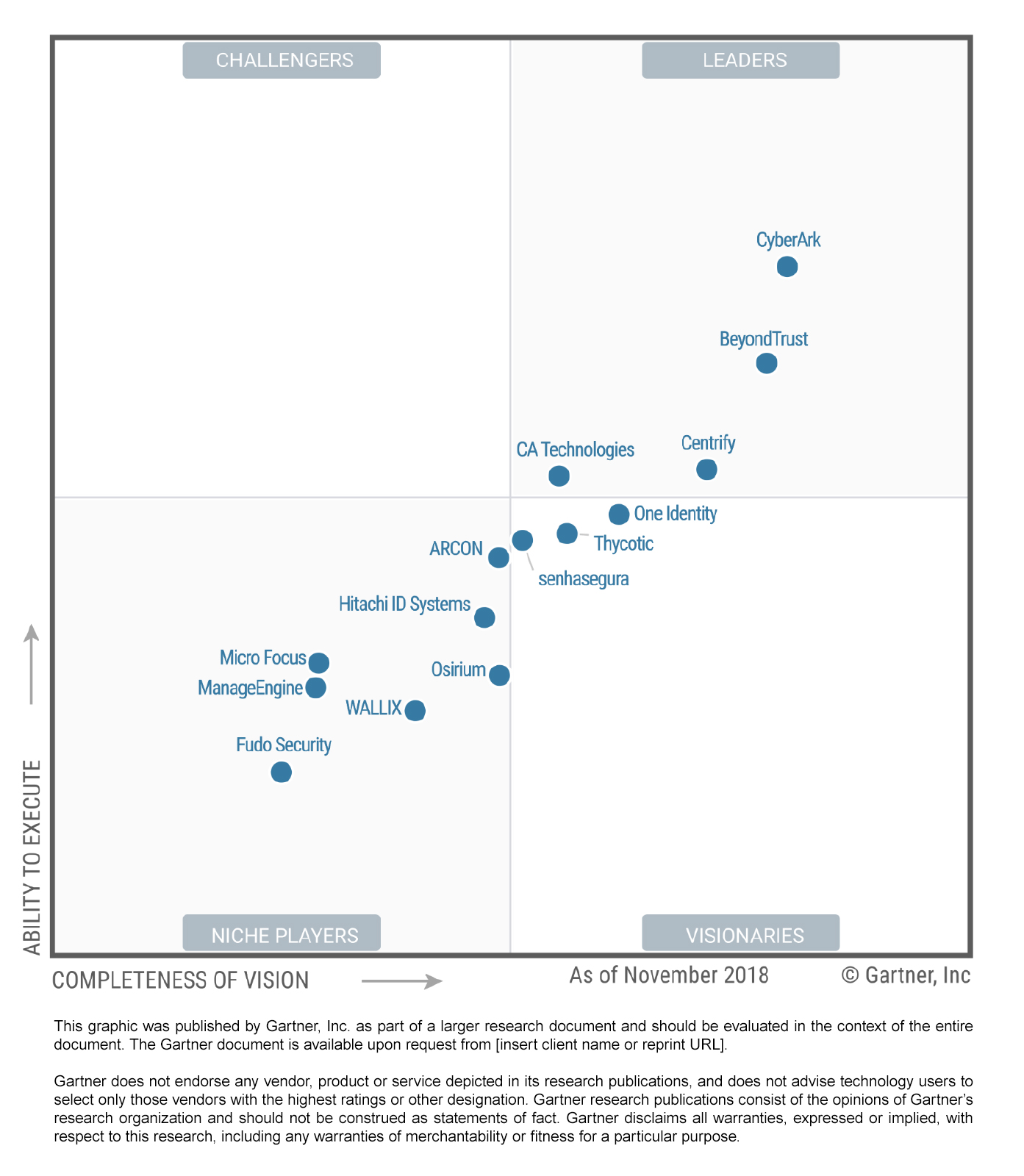
Devolutions Listed in Gartner's Magic Quadrant for Privileged Access Management - The Devolutions Blog